Be Secure
Latest News
IT SECURITY GUIDANCE FOR REMOTE WORK
University employees have the ability, in many cases, to access the University’s information systems from computing devices and locations other than their regular workspace and outside of the University’s network.
Remote access puts systems at higher risk for attacks and unauthorized access because if the system is accessible to employees/faculty and students from outside of the University’s network, it is also accessible to hackers and criminals. This translates to an increased likelihood that University information could be impacted from a confidentiality, integrity, or availability perspective. Additional precautions should be taken by employees when working remotely.
Security Measures
If you access University information systems remotely from a non-CSUDH device, the Information Security Office encourages you to consider the following:
- Use anti-virus/anti-malware software and configure it to automatically update.
- Configure your operating system and applications to apply automatic updates (e.g., Microsoft updates or Mac updates).
- Don’t use the “remember my password” feature when accessing University information on a shared device.
- Download free antivirus below, or email ISO@54zhangmi.com to request campus enterprise antivirus. (For Mac and windows)
Follow these security tips when using CSUDH devices:
- Don’t share or re-use passwords used to access University information and systems.
- Protect passwords used to access University information.
- Consider using a password manager.
- Password Safe is free and available for Windows Users.
- Use encryption whenever possible when storing University information on portable devices.
- Use anti-virus/anti-malware software to scan portable storage devices, e.g., USB drives or external hard drives when you first plug them in.
- You should not consider your online activity to be private when using public Wi-Fi networks.
- Use VPN software to protect your communications when you connect to public Wi-Fi networks.
- Use eduroam to connect to Wi-Fi if visiting participating campuses and institutions worldwide. Connect using your CSUDH credentials.
- If a device containing University information is lost, stolen, or compromised report the incident to the appropriate delegated authority. Please send an email to ISO@54zhangmi.com
- Email Security – Do not send Level 1 information (confidential data) in an email message and be on alert for phishing scams. Report any suspicious emails to ISO@54zhangmi.com.
- To request secured Dropbox folder, or Secured data Transfer visit ACCESS REQUEST WEBPAGE.
Securing Zoom Meetings
CSU message on appropriate practices to prevent Zoom-bombing
It is important to consider the security implications of the Zoom meetings that you set up. Participants may share sensitive data and if you are recording the meetings, the data will be stored. Preventing uninvited guests from joining and sharing the recording via Dropbox will help keep your meeting secure.
FBI Warning of Virtual Hijackers
The FBI has issued a warning regarding cyber actors who "will exploit increased use of virtual environments". Beware of intruders who will hijack your Zoom meetings and disrupt "by inserting pornographic images, hate images, or threatening language."
Zoom Security and Zoom Acceptable Use Policy
Keep out Zoombombers! We highly recommend that you check "Only authenticated users can join" when scheduling Zoom sessions. Authentication requires participants (faculty/staff/students) to Sign In to join Zoom. You can still invite participants who do not have a CSUDH log-in to your Zoom session (outside users can Sign In using Google, Facebook, or another Zoom account).
How Do Users Join Meetings via Authentication?
Users can authenticate, when prompted to Sign In, using the following options:
- CSUDH Users – Select SSO and Enter ‘CSUDH.zoom.us’ and use your campus portal username and password
- Non-CSUDH Users – Select Google or Facebook to use these accounts. Users may also use their company/school zoom.us account. (Users may contact their local Zoom administrator for support)
Visit the IT Zoom Knowledge Base for more information on Zoom.
Zoom Acceptable Use Policy
Zoom has a very strong and professional Acceptable Use Policy that governs all uses of Zoom services. This policy defines the standards Zoom expects its Customers and End Users to adhere to while using Zoom services. Included in this policy is the Reasonable Use information stating that “Zoom provides video conferencing services for business collaboration. Zoom anticipates that customers will use the services in a reasonable manner, given the business purpose. As such, Zoom may limit, suspend or terminate access if an End User’s use exceeds reasonable standards…”
IMPORTANT: It is critical that you read and adhere to the Zoom Acceptable Use Policy at all times when using your Zoom account.
- Do NOT host meetings using your Personal Meeting ID (PMI). Instead use Zoom random meeting IDs for meetings.
- Require a password to join your meeting.
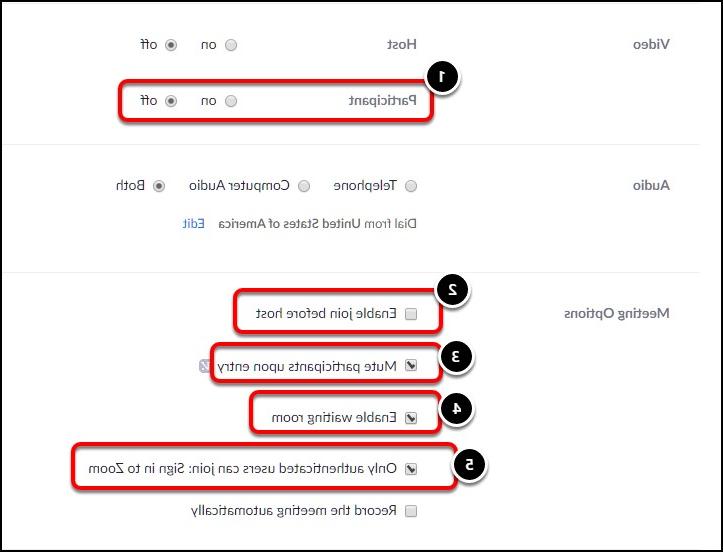
- check Enable waiting room to place attendees in a waiting room when they join. NOTE if you do this, you will need to manually admit each attendee into the meeting. This adds security to the meeting, and you can request users to update their name on the participation list before they join the actual meeting.
- Manage participants in meetings by muting participants, putting participants on hold, and more.
- When using Zoom for classes (Faculty), share the session link only in Canvas.
- Remove disruptive participants. On the Zoom control panel, click on “Participants”, then select “More”, and “Remove” the participant.
- Control screen sharing for participants. The Zoom default allows only the host to share screens. Please only share the screen you select and when needed.
- Turn off the Video for participants. Participants will still be able to use video if needed, but the video option is turned off when a participant joins the meeting.
- Uncheck the Enable join before host option. You should not allow anyone to join the meeting before you have started it.
- Always check Mute participants upon entry. Participants will still be able to use their audio to speak if needed, but they will be muted when they join the meeting.
- Always check Only authenticated users can join. This means that users must have a Zoom account in order to join the meeting. This keeps "guest" accounts from joining your meeting.
Participants
It is very important to make sure that we are properly accounting for the participants in our meeting. If, despite these precautions, someone shows up in your meeting that you don't know, you should take it seriously, because it's possible that these incidents may constitute a phishing attempt to obtain confidential information or access to CSUDH services.
Recordings
If you set up a video meeting, it is important to secure the recording, especially if employee and/or student health data is involved or non-CSUDH participants are attending your meetings.
Dropbox
CSUDH Dropbox, also known as CSUDH Dropbox for Business accounts, is a cloud-based storage solution for students, faculty, and staff. Dropbox for Business offers unlimited storage and file-sharing capabilities for any size file, collaboration with team members, and the ability to showcase projects with partners and clients. Use your campus credentials to login and access files anytime, anywhere form any device, and changes sync across devices.
Dropbox is the only university approved cloud storage for to store Level 1 information as defined in the CSU Data Classification Standard. This information includes any information that is governed by federal, state or local law, or regulated by industry.
Dropbox is approved for HIPAA data.
The responsibility for storing and maintaining documents and files resides with the person who stores the documents. Judgment is required about how and where campus information will be stored.
- Personally Identifiable Information (SSN, account numbers, birth dates, driver’s license numbers, etc.)
- Payment Card Industry Information (Credit Card Numbers, PINs, verification codes etc.)
- Export Laws: Data subject to United States export control or trade embargo regulations.
- Campus Authentication Credentials: This would be the campus issued account and password used to access your computer and email.
- If you are unsure if you are handling legal or CSU protected data, please review the CSU Data Classification Standard and/or contact the campus Information Security Office.
CSUDH Dropbox users are able to open Microsoft files using the Dropbox web interface- See New Dropbox + Microsoft 365 integrations.
ALL Faculty and staff
Currently Enrolled Students
GET HELP

IN-PERSON
Location & Hours
NSM C-151
Monday-Friday, 8 AM - 6 PM

PHONE
(310) 243-2500
Monday - Friday,8 AM - 6 PM
Saturday - Sunday, 9 AM - 6 PM

